2016 has seen its fair share in ransomware attacks. It is already the most attacked year in history and we are only in May! Dial a Nerd and our customers are not invincible to attacks and in the case of ransomware, prevention is better than cure. We have gathered some more types of ransomware that have done the rounds since April.
In a ransomware attack, victims—upon seeing an e-mail addressed to them—will open it and may click on an attachment that appears legitimate, like an invoice or an electronic fax, but which contains the malicious ransomware code. Or the e-mail might contain a legitimate-looking URL, but when a victim clicks on it, they are directed to a website that infects their computer with malicious software.
TeslaCrypt
In its early forms, TeslaCrypt targeted game-play data for specific computer games. It then evolved to affect newer file formats such as Word, PDF, JPEG, and other files. In all cases, the victim would then be prompted to pay a ransom of $500 worth of bitcoins to obtain the key to decrypt the files.
In May 2016, the developers of TeslaCrypt shut down the ransomware and released the master decryption key, thus bringing an end to the ransomware. After a few days, ESET released a public tool to decrypt affected computers at no charge. This tool can be downloaded here: http://download.eset.com/special/ESETTeslaCryptDecryptor.exe
DMA Locker
Although TeslaCrypt called it quits recently, there is new ransomware out there already, DMA Locker. This threat first appeared in January, but its encryption implementation was so flawed that it was hard to take it seriously. Researchers had no problem developing a file recovery tool for the first two versions.
However, its authors have recently fixed all issues and malware researchers believe that with the newly released version 4, DMA Locker has reached maturity and might be the next thing to hit users in widespread attacks.
Like most ransomware, DMA Locker uses emails such as the following. Always check the sender is coming from a legitimate address. In the below example there are strange numbers and lettering.
If you open the attachment you will unleash the ransomware and receive the following message:
Samsam
April’s ransomware attack at Maryland’s MedStar Health hospital network is a prime example. For more than a week, 10 hospitals operated without access to their central networks, because the Windows servers controlling MedStar’s domains were locked down by the ransomware variant known as Samsam. Security firms report that there have been many other incidents with Samsam over the past few months. Some attacks have encrypted the contents of hundreds of servers and desktops.
The Samsam attacks have been so effective in part because the attackers have been able to gain administrative access to the Windows domains they’ve hit by taking advantage of a collection of relatively well-known exploits.
Samsam doesn’t get into your system via mail or software downloads. The best thing to do is to run a scan on your computer and pick any possible corrupt files and remove them immediately.
Amazon Phishing
A new ransomware attack targeting Amazon users has been detected, using a spoofed sender address. Ironically, the campaign has surfaced just as new survey numbers show that most consumers are clueless about ransomware and what to do about it.
Comodo Threat Research Labs said in an alert that a rash of phishing emails have been sent to users supposedly originating from Amazon.com. Reportedly, there is nobody to the email, but the subject is “Your Amazon.com order has dispatched (#code).” The components that do the damage are the attachments, which are included as Microsoft Word documents.
“This latest attack only increases the call to action to strengthen security measures,” the researchers said. “Cybercriminals adapt to attempts to block them, constantly creating new and more insidious strains of malware.”
Cerber
The latest versions of ransomware come so meticulously coded with strong cryptography that it is difficult to find a way around it, so many companies and victims prefer to pay up rather than lose valuable files, but the international cybersecurity community is constantly developing ways to decrypt malware and generally advises victims not to pay.
So if victims are refusing to pay to decrypt their files, cybercriminals have found another way to make trouble. According to researchers from enterprise security software firm Invincea, attackers have modified the existing Cerber ransomware so now, not only does it hold a victim’s files and PC hostage, but the new malware variant also quietly starts sending out a huge amount of network traffic from the infected PC.
The Cerber phishing emails look more legitimate than other ransomware. Do not click on their links! If you are weary, call the company that is billing you to double-check you owe money.
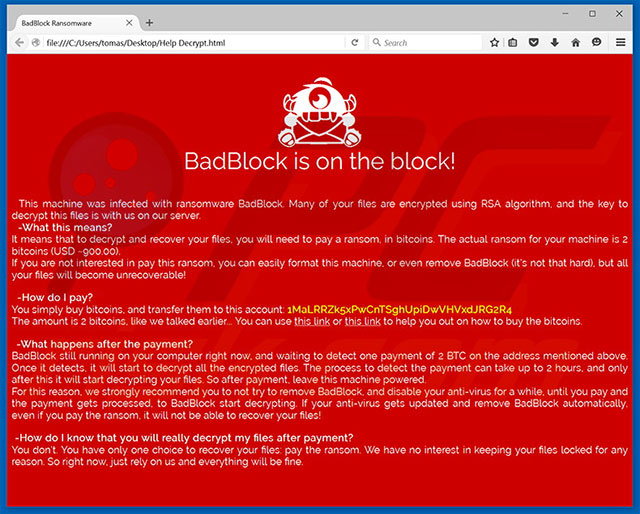
Badblock
This newcomer to the ransomware circle has been reported to be infecting individual home users through URLs that appear to be from fake Adobe Flash Player updates. Users can also get infected through spam emails carrying attachments such as archive, HTML and .exe files posing as legitimate applications. Users can also be affected by clicking on spam links such as those spread on website comment sections and ‘shares’ from infected social media accounts.
Unlike other ransomware like Locky, TeslaCrypt, KimcilWare, PETYA, Mischa, and CryptXXX, BadBlock does not append a custom extension to the encrypted file.
It changes the computer’s wallpaper to a red lock screen and grabs the victim’s attention with the caption, “Badblock in on the block!”
After rendering the files inaccessible, BadBlock demands a ransom of two bitcoins (or $900, according to the ransom note). The user is also provided with helpful links on how to buy bitcoins and how to transfer them to the attacker’s account.
The ransom note further explains that the decryption process will only start upon verification of payment, which it says can take up to two hours. It also warns, “If your anti-virus gets updated and remove BadBlock automatically, even if you pay the ransom, it will not be able to recover your files!”
If you click on these fraudulent mails, you could be taken to screen prompting you for sensitive account information. Always check the URL on the top bar to see if it matches the information on the screen, especially if you have clicked on a link in an email asking for sensitive information.
Some steps to specifically protect yourself from malware are:
- Backup data often. Minimally follow the 3-2-1 rule, maintaining at least three copies in two different formats with one copy stored off-site.
- Some ransomware infects only local drives and mapped network drives, including Dropbox. Company IT services should secure shares by only allowing writable access to the necessary user groups or authenticated users. For Dropbox and Google and iCloud drives, choose to pause syncing whenever possible.
- IT services should block TOR since the TOR network and TOR proxy servers are routinely used by most ransomware.
- Make sure to scrub the malware from all devices on your network before recovering from backup.
- Be wary of emails, even if they refer to mutual friends or familiar services; you may be a victim of spear phishing. Do not click on links in emails before verifying that the website is OK, and do not download email attachments without verifying the source.
- Keep software up-to-date. This will not protect against zero-day exploits, but it will patch the more recent vulnerabilities in your software.
- Use multiple antivirus products to increase your chances of nipping an infection in the bud.
- Install advanced email spam filtering.
- The software should be licensed to guarantee updates. Updated software is much less vulnerable.
Need anti-virus or anti-spam? Fear you may have been hacked? Contact Dial a Nerd today.



